Hi there “Process Automation” fans,
Welcome to a new installment of “Process Automation” tips.
Connections help you grow, and this post shares an insider’s trick to gain access to OTDS administration. If I had known this before it would save me (and probably you too) tons of typing over all these years!
This post is exactly the reason to share information online (outside the OpenText cocoon). This stuff helps others, and we now get a tip because someone accidentally sees what we’re doing, otherwise we would have never known. Don’t keep information inside the company; We are developers that need to promote the products at your customers, and this is exactly what limits us! That’s the same for the licensing part…Give your valuable developers an unlimited dev-license to build POCs, share thoughts, try-out stuff, and bring the platform to a new level….Please!
Let’s get right into it…
What am I talking about? Well, you do know this OTDS login screen…right?
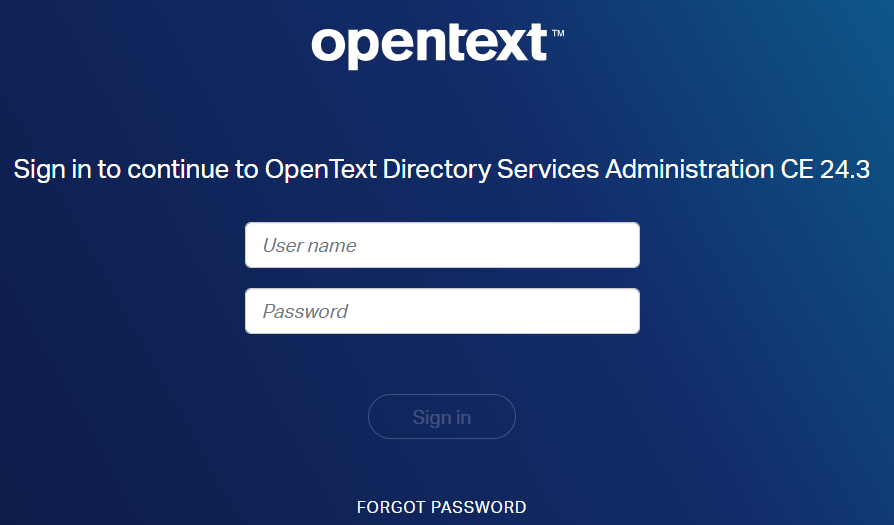
It’s behind a URL like this:
http://192.168.56.107:8181/otds-admin
For administrator access you would fill in this account name otadmin@otds.admin with the corresponding password…correct?
…
- Before you continue…
- Hold yourself inline…
- Don’t jump off the building…
- Take a deep breath…
- Don’t jump off the building…
- Hold yourself inline…
…
Well, what if I tell you this account name is replaceable with admin! WHAT!?!? No way?? Yes, it is…try it out and check the result:
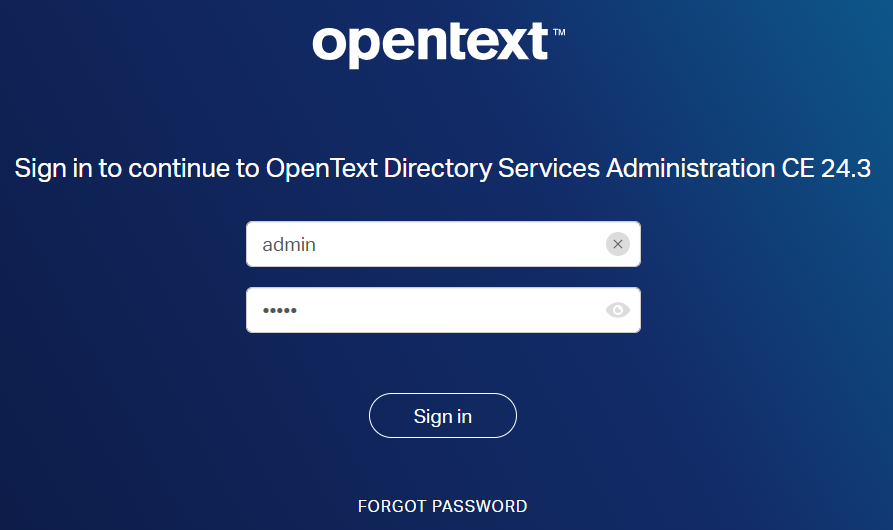
After login, you’re nicely connect with the otadmin account…It’s an amazing discovery!
Remote debugging time
Now, I’m off-course very curious where to find the implementation part in the code-base of OTDS!? So, this is my first point of entry of bash commands finding some interesting JAR files:
1 | #To find the JAR containing 'otadmin' |
They show me interesting insights on OTDS classes and the authentication after a too long remote debug session; Only, I could not find the answer!
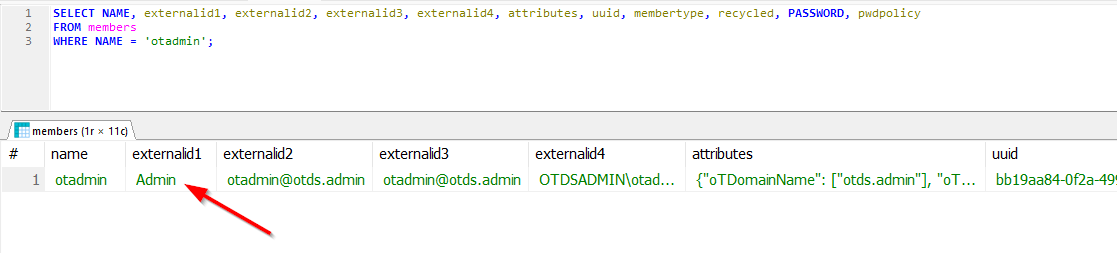
After a 🍹 and my learnings from remote debugging, I got a burning light in my head about LDAP; In the past, OTDS used OpenDJ as LDAP-interface and from my CARS experiences (also LDAP; but over OpenLDAP), I know authentication passes here. Now OTDS replaced OpenDJ with a database implementation, so that’s my next move where I quickly found out about the table behind this query:
1 | SELECT NAME, externalid1, externalid2, externalid3, externalid4, |
See the result, and now you guess how to login when we manipulate this externalid1 to a value of YOLO!!
Is it wisely? I don’t think so; Is it possible? Only one way to find out:
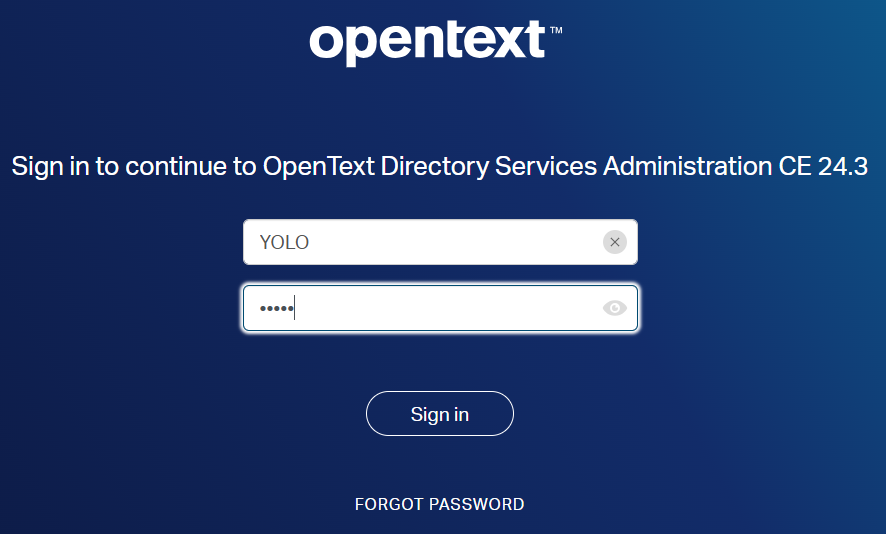
Did it work?…OWHHH YEAH! 😎
…
For your reference on OTDS/CARS and the LDAP connection strings from the past (maybe it helps somebody…have a comment!):
2
3
4
sudo yum -y install openldap-clients
#This is for CARS over OpenLDAP as LDAP interface
ldapsearch -H ldaps://opa.mydomain.com:6366 -D "cn=Directory Manager,o=mydomain.com" -w admin
Again, a fascinating “DONE” where we found ourselves a new way to log in to OpenText Directory Services with a little help from a connection (you know who you are). After this quick deep dive, we even understand where it gets the value from and even how we can manipulate it. I say, let’s continue next week into some other great topic about “Process Automation Tips”…
Don’t forget to subscribe to get updates on the activities happening on this site. Have you noticed the quiz where you find out if you are also “The Process Automation guy”?


